
For a digital business, such as a development company like ScreamingBox, or like many of our clients with digital apps and e-commerce sites, a cyber security attack can really damage a business.
As you might know, a cyber security attack is the deliberate abuse of computer systems, networks and other technology dependent undertakings, using malicious coding to modify a computer program or application’s code, data and/or logic. Cyber security attacks and incidents may also be referred to and categorized as Cyber-Attacks, and come in many forms and types.
Cyber security attacks not only affect the normal operation of your computer programming, these attacks peak into destructive consequences that compromise data and promote cybercrimes such as information and identity theft.
In some scenarios, sensitive data has been exposed as a result of cyber security attacks promulgated by security attacks. In recent years, high profile cyber-attacks have provided hackers with private data, which they in turn have used to illegally access funds as well as other potentially damaging actions.
For instance, the 2017 Equifax breach compromised the personal data of an estimated 143 million consumers, including birth dates, addresses and Social Security numbers. In 2018, Marriott International disclosed that hackers accessed its servers and stole the data of roughly 500 million customers.
Here are 7 common security attacks that can kill your business:
Phishing
This refers to a type of social engineering where hackers disguised as reputable entities or individuals, send mass fraudulent emails to unsuspecting users with the aim of distributing malicious links. When opened, the link distributed can perform a variety of functions, including; extracting login credentials, access to private data and financial account information from victims.
Once the victim opens the said malicious link, the computer system could be frozen, as part of a ransomware attack, access to sensitive information could be acquired and installation of malware.
Phishing attacks can also be executed via phone calls and via text message, and this is referred to as voice phishing and SMS phishing respectively. There are different types of phishing attacks and these include;
Spear Phishing – Spear phishing is distribution of emails containing malicious links, targeting a particular individual or organization, with the goal of accessing unauthorized crucial information, trade secrets, military intelligence etc.
Whaling – This type of phishing targets on high-profile employees such as senior executives and stakeholders in organizations. This is aimed at stealing vital information since those holding higher positions in a company have unlimited access to sensitive information.

Malware Infection
Malware infection can also be referred to as malicious software, which is any program or file that is intentionally harmful to a computer. Malware code is activated when a user clicks on an unprotected links or attachment, resulting into installation of malicious software.
The term malware encompasses various types of cyber security attacks including; Trojans , Worms , Adware , Ransomware, Spyware and various types of computer viruses.
A computer that has been compromised by malware infection can:
– Make the system inoperable.
– Install additional harmful software.
– Block access to key network components.
– Secretly obtain information by transmitting data from the hard drive
An example of Malware is the CovidLock ransomware 2020 . The fear of the Covid 19 pandemic among the masses was greatly exploited by cyber criminals. This type of ransomware infected victims via malicious files promising to offer more information about the disease. However, once installed, CovidLock encrypts data from Android devices and denies data access to victims. To be granted access, the victims had to pay a ransom of USD 100 per device.
Spyware Infection
Spyware can be defined as malicious software designed to enter your computer device, gather data about you and forward it to a third party (hacker) without your consent. Some of the data collected may include; log in credentials, bank details, emails sent and received, sites visited, things downloaded and much more. The information gathered is always used by the hacker to blackmail the victims as well as carrying out other atrocious cybercrimes.
Spyware is often installed onto your PC and mobile device through clicking on malicious links, and goes to operate by running quietly in the background of the compromised device.
Man-in-the middle (MitM) Infection
This kind of security attack occurs when a hacker intercepts correspondence between two unaware victims, inserting himself / herself in the middle with the intention of blackmailing and exploiting both parties.
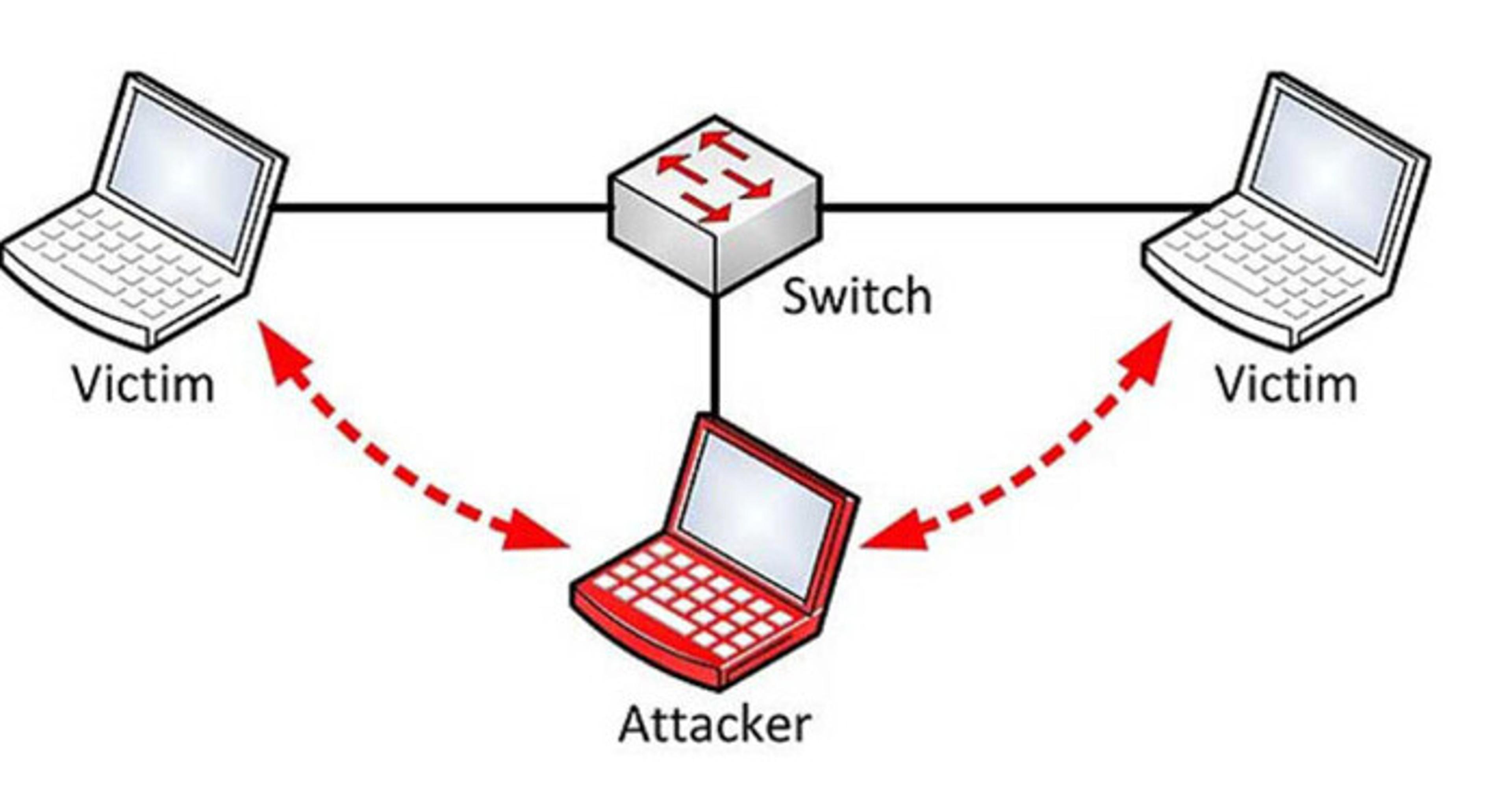
This attack exploits the existing security vulnerabilities such as unsecure public Wi-Fi, to gain access to the targets’ device. Unfortunately, detecting MitM infection is not an easy task since, both parties believe they are corresponding with each other, and the data is being transmitted to a legitimate location.
In most cases, phishing and malware attacks are often used to later carry out MitM infections.
Denial-of-Services (DOS) Infection
A denial of service (DoS) infection is a type of cyber-attack that floods a computer’s system, servers or network with traffic to overload resources and bandwidth. The result is always rendering the system unable to process and fulfill genuine requests.
In addition to denial-of-service (DoS) attacks, there are also distributed denial-of-service (DDoS) attacks. DDoS attacks are launched from several infected host machines with the goal of achieving service denial and taking a system offline, thus paving the way for another attack to enter the network/environment.
Survey Query Language (SQL) Infection
This security attack occurs when a hacker inserts malicious code into a server using survey query language, prompting the server to deliver protected information. Such data may include numerous items such as private customer details, user lists, or sensitive company data.
SQL infections are detrimental to a business since they result into deletion and exposure of important information which could result into loss of clients’ trust.
Network Cyber-Attacks usually are focused on a business’s computer networks versus attacking a single computer or device, and are an indicator that the business’ systems and data have been compromised or that the measures put in place to safeguard them have failed.
Password Attack
A password attack simply means an attempt to decrypt or obtain a user’s password with illegal intentions. With the right password, a cyber attacker has access to a wealth of information. Password attackers use methods like; social engineering and dictionary attack to identify the password.

Conclusion
Cyber-Attacks are a serious threat to businesses of all kinds, and especially for digital businesses such as SaaS applications, e-commerce, fintech and mobile apps. Make sure you understand the different types of cyber security attacks that are out there, and make sure your DevOps and developer teams are aware of the latest threats and are writing clean secure code and updating all network security functions.
ScreamingBox's digital product experts are ready to help you grow. What are you building now?
ScreamingBox provides quick turn-around and turnkey digital product development by leveraging the power of remote developers, designers, and strategists. We are able to deliver the scalability and flexibility of a digital agency while maintaining the competitive cost, friendliness and accountability of a freelancer. Efficient Pricing, High Quality and Senior Level Experience is the ScreamingBox result. Let's discuss how we can help with your development needs, please fill out the form below and we will contact you to set-up a call.