How to Build Zero Trust APIs for Microservices: A Practical Security Guide for Modern Teams

When APIs Behave Like Overly Trusting Golden Retrievers
In a perfect world, every API in a microservices architecture would behave like a well-trained security guard: alert, skeptical, and definitely not handing out access to anyone who looks “kind of familiar.” Unfortunately, many APIs resemble the opposite - an overly trusting golden retriever who lets anyone in as long as they have a vaguely friendly vibe.
Developers know this feeling all too well. One forgotten authentication check, one overly permissive rule, or one “temporary” token that never gets rotated, and suddenly a microservice environment becomes less a fortress and more an open house.
That’s where Zero Trust API design enters the scene - part bouncer, part detective, and part overly cautious grandmother who needs three forms of ID before letting someone sit on the couch. While the term can sound intimidating, Zero Trust isn’t about making systems unfriendly. It’s about ensuring that every service - no matter how small, internal, or seemingly harmless - authenticates, authorizes, and verifies every request.
This guide walks through how modern engineering teams can build Zero Trust APIs in microservices using token-based authentication, robust service identity, and mutual TLS. And yes, the golden retriever can stay - but only after passing a very strict background check.
Why Zero Trust Matters for Microservices
Microservices multiply quickly. As organizations scale services, deployments, and teams, API endpoints become the connective tissue that makes everything work. Unfortunately, that same connective tissue is also an attractive target for attackers.
The Increasing Vulnerability of API Endpoints
APIs are frequently the weakest link because they expose predictable, callable interfaces. When each service communicates through APIs, the surface area expands - which means more entry points, more tokens, more traffic paths, and more complexity to manage securely.
Zero Trust helps reduce the risk by assuming two things:
- No service should be trusted implicitly, even inside the cluster.
- Identity must be verified continuously, not just at login or deployment.
This mindset aligns with modern security best practices and regulatory expectations. It also serves a practical business purpose: lowering breach risk improves uptime, customer trust, and the cost efficiency of maintaining secure services at scale.
What Zero Trust Means in an API Context
Zero Trust for APIs requires more than a firewall or a gateway. It’s a combination of security layers, each reinforcing the other.
Core Principles Applied to Microservices
Zero Trust implementation for microservices typically relies on:
- Strict authentication and authorization for every request, both external and service-to-service.
- Granular identities assigned to each service or workload.
- Encrypted communication using standards like TLS or mTLS.
- Policy-based access control, including role-based and attribute-based models.
- Continuous verification, monitoring, and auditing.
These principles form the foundation for modern Zero Trust API design and support scalable, secure microservices without slowing teams down. If you want more info on API Microservices, then check out our article on Microservices vs. Monolithic Architecture .
Building Zero Trust APIs: A Step-by-Step Framework

This section outlines three core strategies - token-based authentication, service identity management, and mutual TLS - that collectively create a strong Zero Trust API security posture.
Token-Based Authentication for API Requests
Token-based authentication is often the first step toward Zero Trust because it provides a reliable way to verify who is calling an API and what they’re allowed to do.
Why Tokens Work Well in Microservices
Tokens are stateless, portable, and scalable - an ideal match for cloud-native architectures. They also allow granular control and can carry metadata about scopes, permissions, or expiration times.
Common Token Types for Zero Trust APIs
JWT (JSON Web Tokens)
Widely used for authentication and authorization, JWTs allow services to verify claims without contacting a centralized server. However, they must be managed carefully - especially regarding expiration and rotation - to avoid becoming a single point of failure.
Opaque Tokens
While less self-contained than JWTs, opaque tokens require a backend validation step, making them harder to forge and easier to revoke quickly.
Best Practices for Token-Based Security
- Enforce short token lifespans to limit risk.
- Rotate signing keys regularly to prevent stale access.
- Use scopes and granular permissions for fine-grained control.
- Validate tokens at every request, even between internal services.
- Avoid embedding sensitive data in token payloads.
Token authentication is a strong starting point, but Zero Trust requires going beyond verifying end users - it requires verifying services themselves.
Service-to-Service Identity Management
In a microservices environment, services communicate with each other constantly. Ensuring each service has a distinct, verifiable identity prevents impersonation and unauthorized lateral movement.
Why Service Identity Matters
Without defined identities, microservices essentially operate on the honor system. Under Zero Trust, no service is considered honest without proof.
Using Identity Providers and Service Meshes
A growing number of organizations use tools like:
- SPIFFE/SPIRE for identity framework and certificate issuance
- Kubernetes Service Accounts combined with policies
- Service meshes (e.g., Istio, Linkerd, Consul) for workload identity and request enforcement.
These tools automate identity issuance, distribution, and rotation, reducing risk and operational overhead.
Key Components of Service Identity
Workload Identities
Each service instance gets its own identity, which proves what it is - not just where it’s running.
Policy Enforcement
Workload identities feed into access control rules such as “Service A may call Service B only when the request matches X attributes.”
Best Practices for Identity Management
- Use automated certificate issuance and rotation - manual processes don’t scale.
- Implement policy as code for traceability and automation.
- Audit and monitor service identities to detect anomalies.
- Keep identities short-lived for better security and less operational risk.
Identity forms the backbone of Zero Trust, enabling the next layer: mutual authentication through mTLS.
Using Mutual TLS (mTLS) for Service Communication
Token authentication verifies application-level identity. Mutual TLS validates identity at the network level - ensuring both sides of a connection are who they claim to be.
Why mTLS Is Essential
TLS alone encrypts data, but only one side verifies identity. With mutual TLS, both client and server authenticate one another. This protects against man-in-the-middle attacks, rogue services, and internal impersonation attempts.
How mTLS Works in Microservices
Client service presents a certificate proving its identity.
1. Server presents its own certificate, which the client validates.
2. A secure, authenticated channel is established.
Service meshes simplify mTLS by handling certificates, rotation, and enforcement automatically - removing the need for developers to manage low-level TLS tasks.
Best Practices for mTLS Implementation
- Automate certificate management to avoid expired certificate outages.
- Use a mesh or identity platform to integrate mTLS with policies
- Monitor mTLS handshake failures for early warning of misconfigurations or attacks
- Ensure certificates are short-lived and rotated transparently
With token auth, service identity, and mTLS working together, organizations can achieve a layered, resilient security posture.
Creating Policy-Based Access Controls
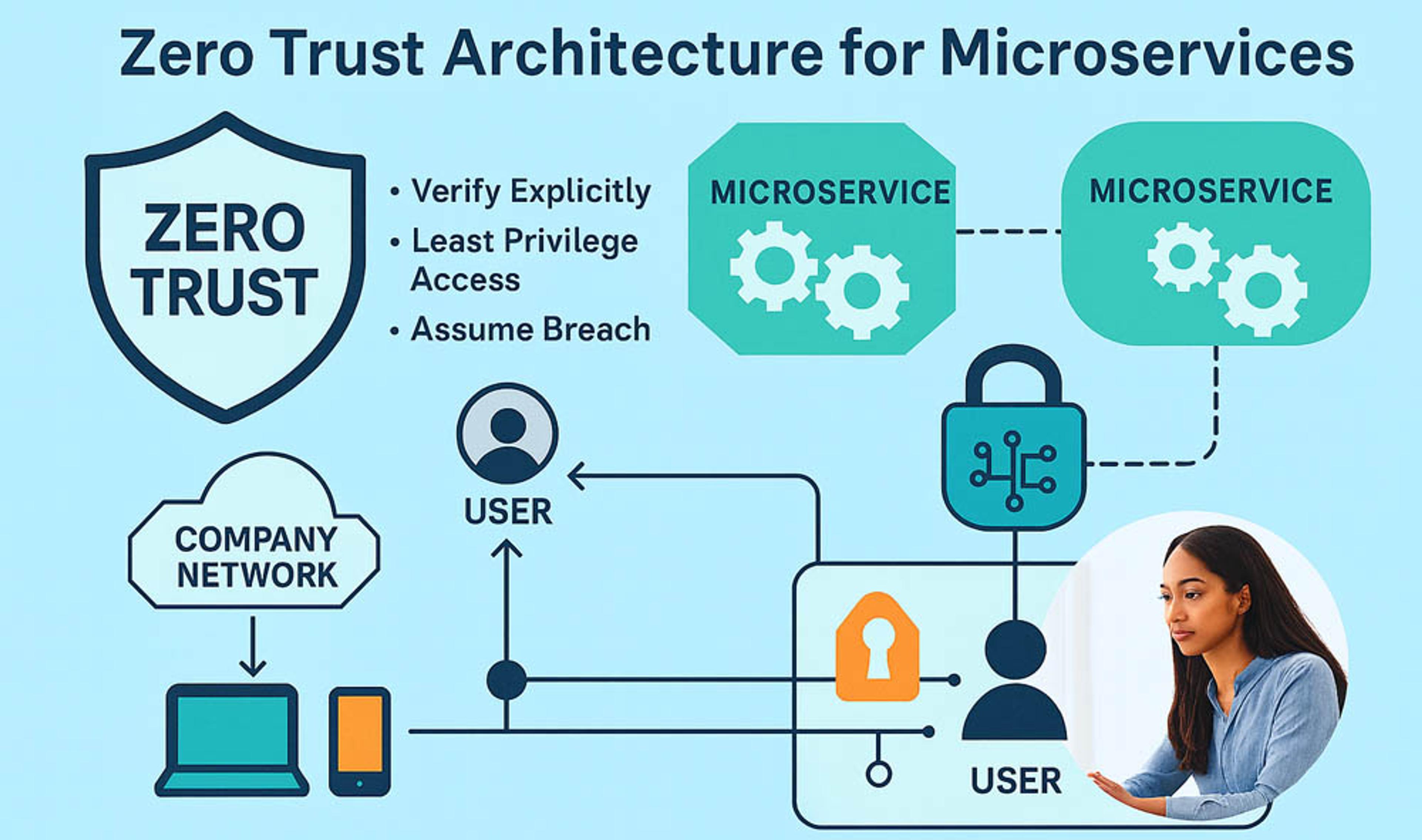
Security policies translate Zero Trust principles into actionable rules for microservices.
Types of Access Controls
Role-Based Access Control (RBAC)
Best for predictable, structured environments. Assigns roles such as “billing-service” or “frontend-api,” then grants permissions accordingly.
Attribute-Based Access Control (ABAC)
Grants access based on attributes like environment (prod vs. dev), service identity, location, or request context.
Implementing Effective Policies
- Start with least privilege - give services only the access they need
- Use environment segmentation to reduce risk of lateral movement
- Implement deny-by-default policies, allowing access only when explicitly permitted.
- Regularly review and refine policies based on usage and log data.
This structured approach ensures reliability and reduces unauthorized access risk.
Observability and Continuous Verification
Zero Trust is not a one-time configuration - it requires ongoing visibility and verification.
Logging and Monitoring
Key metrics include:
- Authentication failure
- Authorization denials
- Unexpected service communication patterns
- Token refresh or rotation errors
- mTLS handshake issues
These signals reveal potential misconfigurations, breaches, or emerging vulnerabilities.
Automation and Alerting
Automated alerts ensure that suspicious events trigger immediate investigation. Integrating logs with SIEMs or cloud monitoring platforms provides full visibility into service interactions.
Practical Example: Applying Zero Trust to a Typical Microservices App
Imagine an application with an API gateway, user service, billing service, and reporting service.
A Zero Trust setup would include:
- API gateway issuing tokens and validating user identity.
- Each service holding a unique workload identity issued by a secure identity provider.
- Services communicating over mTLS, ensuring encrypted and authenticated connections
- RBAC policies defining which services can call which endpoints.
- Monitoring tools tracking authentication requests, token expiration, and abnormal behavior.
This architecture enables secure, predictable communication across a growing set of microservices.
Conclusion: Zero Trust APIs - Practical, Scalable, and Essential

Zero Trust isn’t about paranoia - it’s about practicality. As systems grow more complex, and microservices multiply, relying on implicit trust becomes risky and unsustainable. By layering token-based authentication, service identity management, and mutual TLS, organizations can harden their APIs, reduce lateral attack risk, and create a more resilient architecture overall.
The path forward is clear: secure every request, validate every identity, encrypt every connection, and enforce every policy. Zero Trust APIs are no longer optional - they’re a business necessity.
For teams looking to strengthen their microservices strategy, the next step is simple: evaluate current API security, identify gaps, and begin implementing these Zero Trust components step-by-step. Every improvement brings the architecture closer to a secure, future-ready foundation - and ensures that even the friendliest golden retriever API learns how to check ID.
To have a deeper conversation about Zero Trust API architecture and other security measures that can be used for your digital development project, please Contact ScreamingBox .
Check out our Podcast on Cybersecurity for a deeper look at various Cybersecurity measures you can take for your company and digital development..
ScreamingBox's digital product experts are ready to help you grow. What are you building now?
ScreamingBox provides quick turn-around and turnkey digital product development by leveraging the power of remote developers, designers, and strategists. We are able to deliver the scalability and flexibility of a digital agency while maintaining the competitive cost, friendliness and accountability of a freelancer. Efficient Pricing, High Quality and Senior Level Experience is the ScreamingBox result. Let's discuss how we can help with your development needs, please fill out the form below and we will contact you to set-up a call.